Protocol defines absolute data security, whether you see it or not

Smooth real-time transmission of video stream is a standard requirement for remote collaboration solutions. Why fulfilling this feature is not sufficient, and why absolute data security is essential in all industrial usage, we will learn all this in this article.
Update October 2022: Delta Cygni Labs released XRTC API and SDK as a new product line, learn more at XRTC.org
Pandemic! Shut-down! Travel restrictions! Real time collaboration across borders and continents has become increasingly important in recent years. Now even the most agile teams are facing difficulties in their cooperation. Companies are presented with great technical and organisational challenges. The solution to these challenges is Remote Collaboration.
Video conferences and meetings have become an integral part of business life, as have remote maintenance solutions. If your company is using one of the consumer grade solutions, every time someone in the company network makes a video call with a customer, an employee or a third-party technician, you have to punch a hole inthe company’s firewall. That has to be for every such collaboration, because the solutions are dependant on the WebRTC protocol which is built on the User Datagram Protocol (UDP). These protocols can never provide absolute data security, because the more contacts you have, the more holes you have to punch:
- If you manage a national or international remote dealer network
- When you instruct external technicians via remote guidance
- If you work across several locations
- When your production or your products are IoT ready
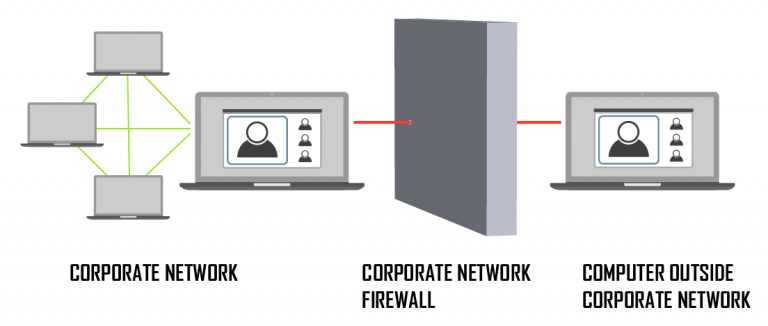
This unavoidable vulnerability of many video collaboration solutions is a result of the protocol used. Therefore the employees working from home offices not only often provide amusing insights into their private lives through insufficiently secured video conferences, but they also give skilled hackers the opportunity to gain deep insights into the company systems and data. In the worst case, attackers can completely take over your system or the Machinery and equipment you supply.
What does protocol mean?
Protocol is the term used to describe the standards and norms that define the way in which data is transferred between different computer components, computer systems and networks on the Internet. Whenever you join a video conference or use a remote maintenance solution, the systems involved have negotiated this protocol beforehand.
What many do not know: The User Datagram Protocol (UDP) used by the vast majority of softwares was developed as early as 1980 and was later used mainly in online gaming. Accordingly, it had to guarantee above all a smooth data transfer. It never had to be particularly secure.
Correct: If you use video conferences, web-meetings or remote guidance solutions, your company’s cyber security depends on a protocol that exists to serve online gaming. A protocol that was adopted by SKYPE some 20 years ago because there was no other protocol to use for real-time communication.
This protocol has major security gaps due to its architecture. The latest attack method is so-called NAT Slipstreaming, which uses the inbound connections essential to UDP based communication as a point of attack. For each inbound connection a “hole” must be opened in the firewall must. Therefore, more contacts your system has outside your network, the more entry points your firewall has to allow.
These holes in the firewall can be monitored, but it takes enormous resources to constantly close the holes caused by UDP based communication. You need some good admins to react on every new challenge. You need state-of-the-art hardware. You or your IT staff need time. A lot of time. And even if you can guarantee these resources NOW for your company – can you also guarantee them for those collaborators sitting in front of their screen somewhere in the world?
Most companies can only answer “no” to this question. As well as the question of how the additional expenses can be managed in the future with the increasing use of remote collaboration solutions – also in regard to new technologies likeIoT, smart factories and smart home.
The alternative for absolute data security: XRTC
There is a protocol that guarantees smooth data transmission and is secure. As the only remote collaboration solution on the market, POINTR uses the XRTC protocol. The XRTC protocol was developed by Delta Cygni Labs from the older Transmission Control Protocol (TCP). Not only its architecture protects against the current NAT slipstreaming attacks pestering UDP based solutions, but because it does not use any inbound connections, it is also protected against all methods that could use this vulnerability in the future.
XRTC was originally developed to ensure communication between European Space Agency sites in different European countries. From the very beginning, the solution had to meet the absolute data security requirements: same level as governmental and military projects. The development therefore followed the Security by Design (SBD) approach. This means that the software was designed from the ground up to ensure that there are no points of attack.
The secure-by-design principle as foundation of XRTC
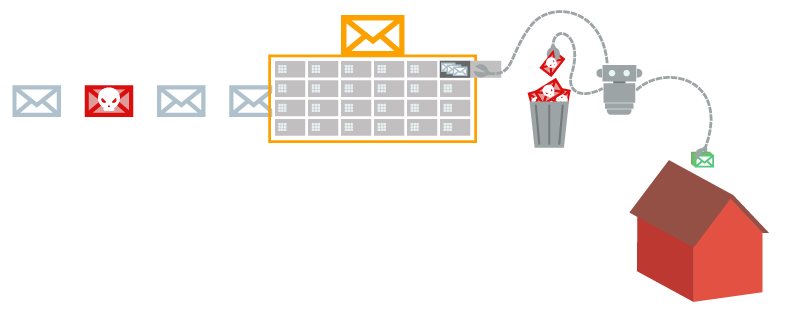
XRTC uses strictly outgoing TLS1.2 connections and thus follows the concept of Poste Restante. In regard to real time digital communication this means that all data packets are stored outside the own network.
In contrast to UDP, the data packets are not delivered “home”, straight to the own address, but the XRTC periodically picks up the data packets from a “PO box” located outside the firewall. In this way XRTC does not allow any external supplier to enter through the firewall, but also does not disclose its address to any one it is communicating with.
The XRTC also solves a TCP problem known among experts as “Head of Line Blocking”. This HoL Blocking is known to the common user as “lagging” – delayed transmission or still images during video conferences and video transmissions.
XTRC and solutions based on it work in all wireless networks (WiFi, 3G, 4G and 5G). In particular, XRTC technology has significant advantages in the 5G network and edge computing. The protocol is not only secure today, but is also built to withstand future threats.
The most secure remote collaboration solution on the market
1. POINTR is the only remote collaboration solution on the market with absolute data security. It is not only 100% protected against NAT slipstreaming attacks, but also completely eliminates attack vectors that rely on that vulnerability: inbound ports that are opened for UDP based protocols.
2. Exchanging content over digital communication solutions is a common and easy attack point for hackers with malicious intents .You can exchange content and avoid security threats with your business partners using the secure way of content sharing: only exchanging the content without sending any files. Just showing content over the communication tool eliminates all threats of sending and downloading files.
3. All handshakes and contacts take place outside your secure network. Potentially infected files stay outside, because ALL files stay outside. All this without admin effort and without the need and expense to constantly update to the latest hardware.
The XRTC protocol used by POINTR – even if you are not yet familiar with it – is already used worldwide in production by well-known customers and has proven itself in commercial operation as well as in demanding security audits and penetration tests.
Learn more about POINTR and the XTRC protocol.
